Introduction
In LayerOps, a service can represent anything that runs on your instances, whether it's an API, a frontend, a job, or anything else. These services are highly configurable and can be deployed from our marketplace or directly from any Docker image.
LayerOps offers three types of services:
- Classic services: The most common type, used for running applications, APIs, frontends, etc.
- Cron services: Designed for scheduled tasks and periodic jobs
- Database services: Specifically tailored for databases, offering features like automated backups and S3 export capabilities
You can either deploy these services from scratch or use pre-configured services from our marketplace. For detailed information about service creation and configuration, check out the service creation documentation.
Detail
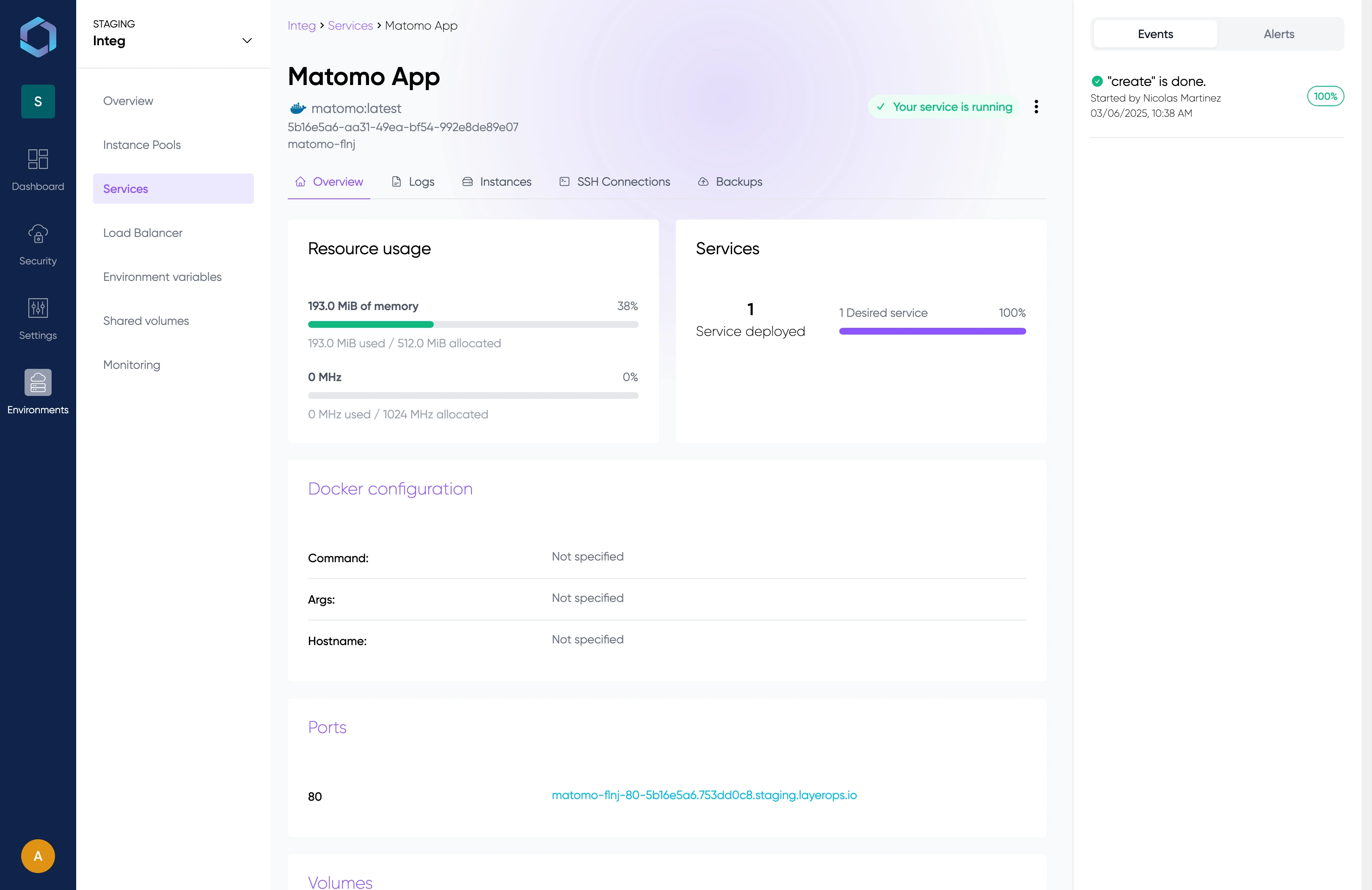
Once created, you can access your service to see all the information: on which instance it is deployed, how many services are deployed, resource usage, etc.
Overview
In "overview" you'll find all the important information about your service. For example, you can find the exposed ports and associated domain names.
You'll also find basic monitoring of the resources allocated and consumed by your service.
Instances
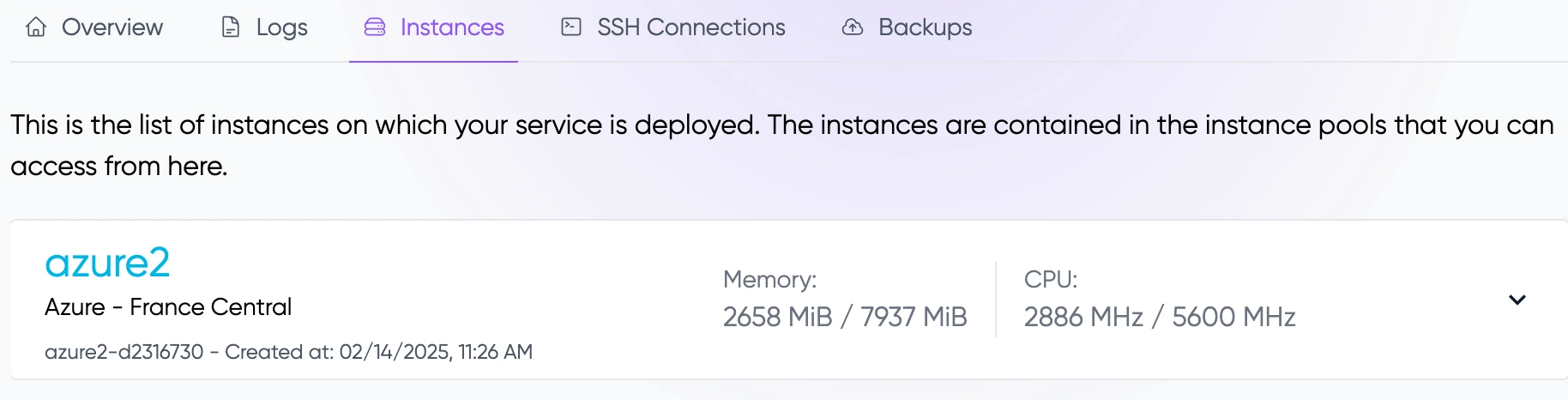
Track where your services are deployed in the "Instances" tab. You can see the distribution across the different providers.
Alerts
Follow real-time alerts related to your service. If your service is configured with autoscaling, these alerts can trigger scale out / scale down, or even scaling on instance pools.
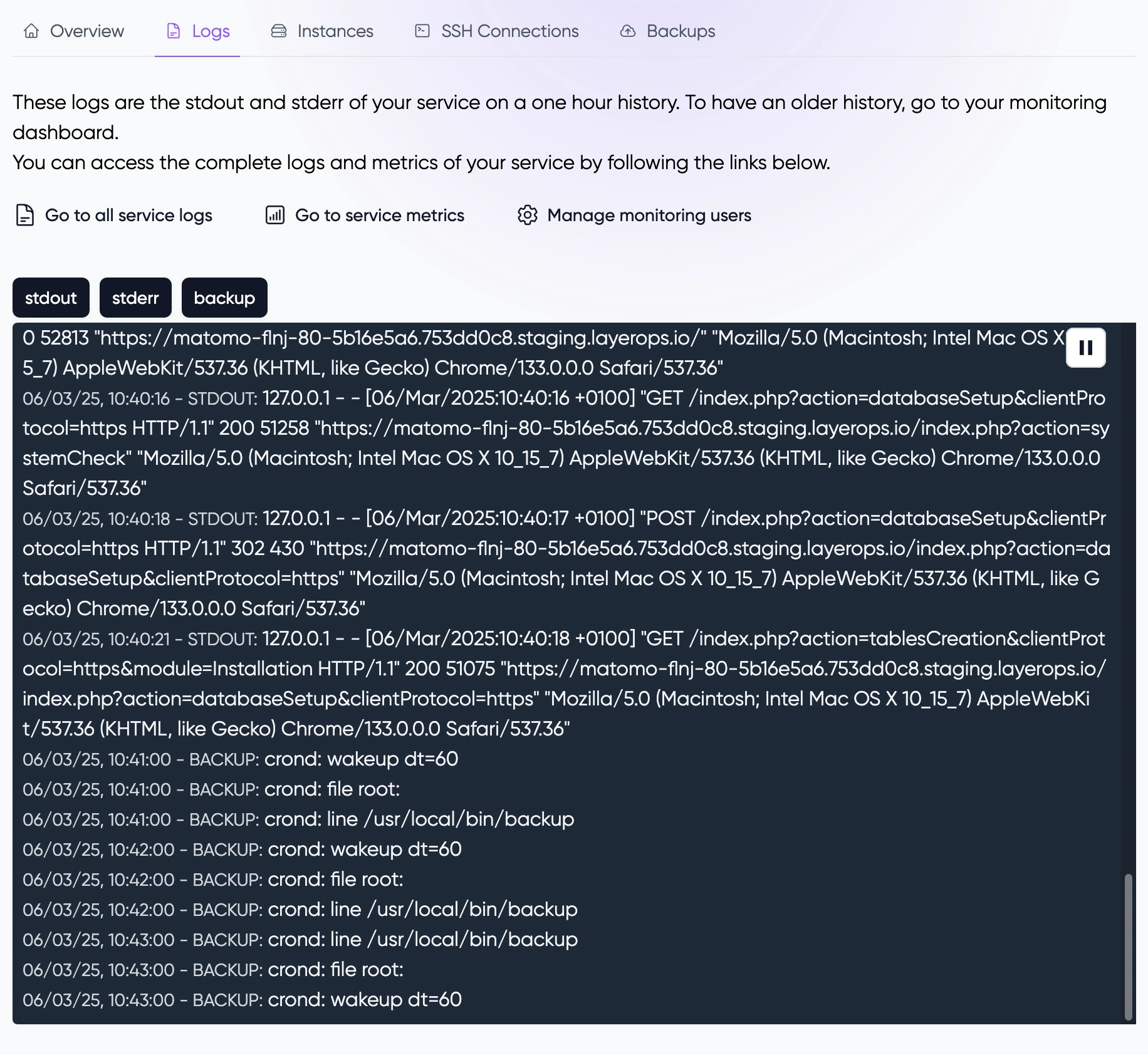
Logs
In the "Logs" tab, you can view your service logs in real-time. This tab also provides direct links to detailed dashboards where you can access comprehensive logs and metrics for your service.
SSH Connections
The "SSH Connection" tab allows you to manage and establish SSH connections to your services. You can view existing SSH connections and create new ones, useful for debugging and troubleshooting purposes.
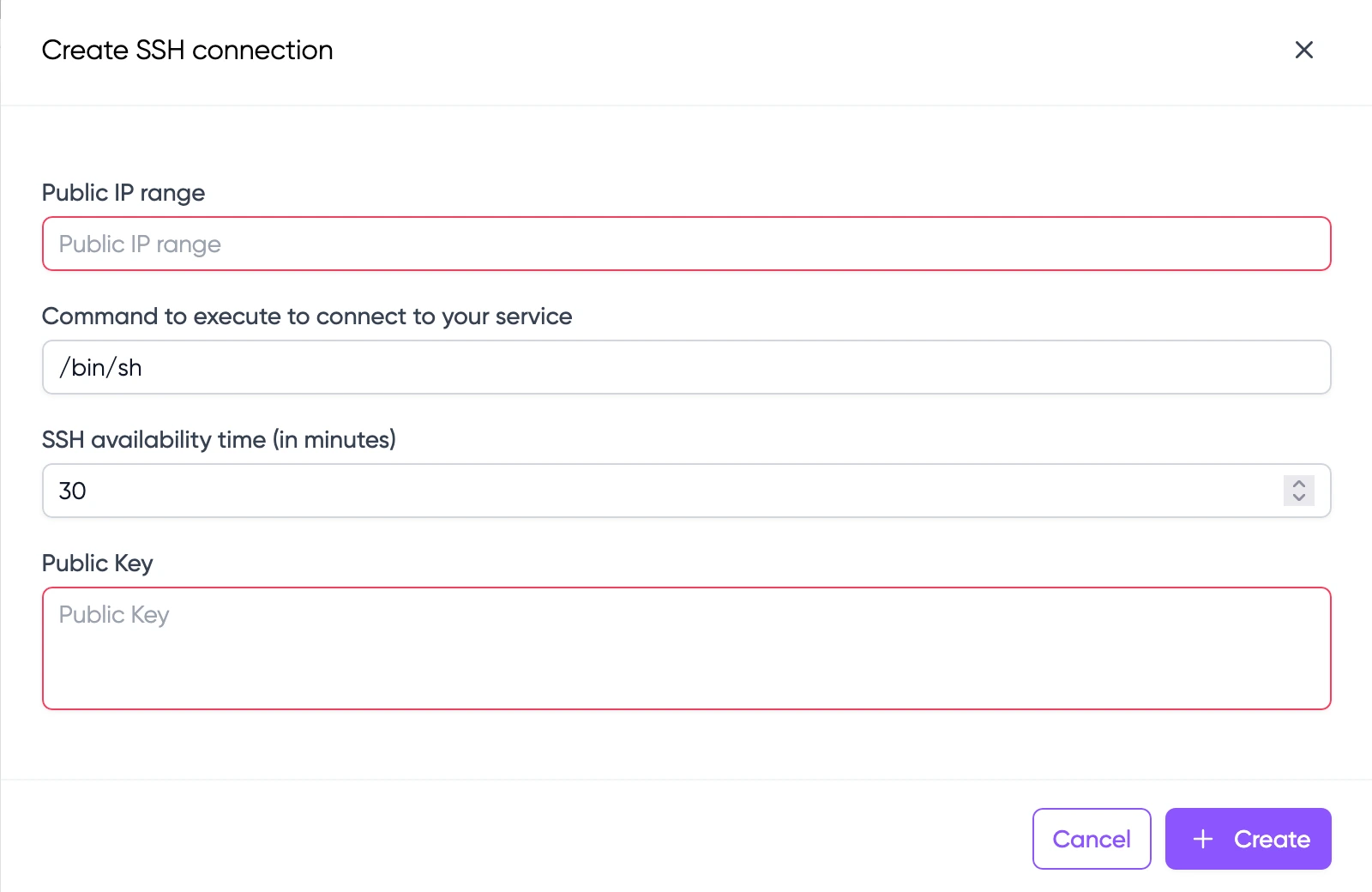
You can easily add SSH connections by configuring an authorized public IP address and associating it with a public SSH key, providing a secure method for connecting to your services.
You can control SSH access through Role-Based Access Control (RBAC). This ensures that SSH connections are authorized only for users with the necessary permissions, enhancing the overall security of your services. Read more about RBAC
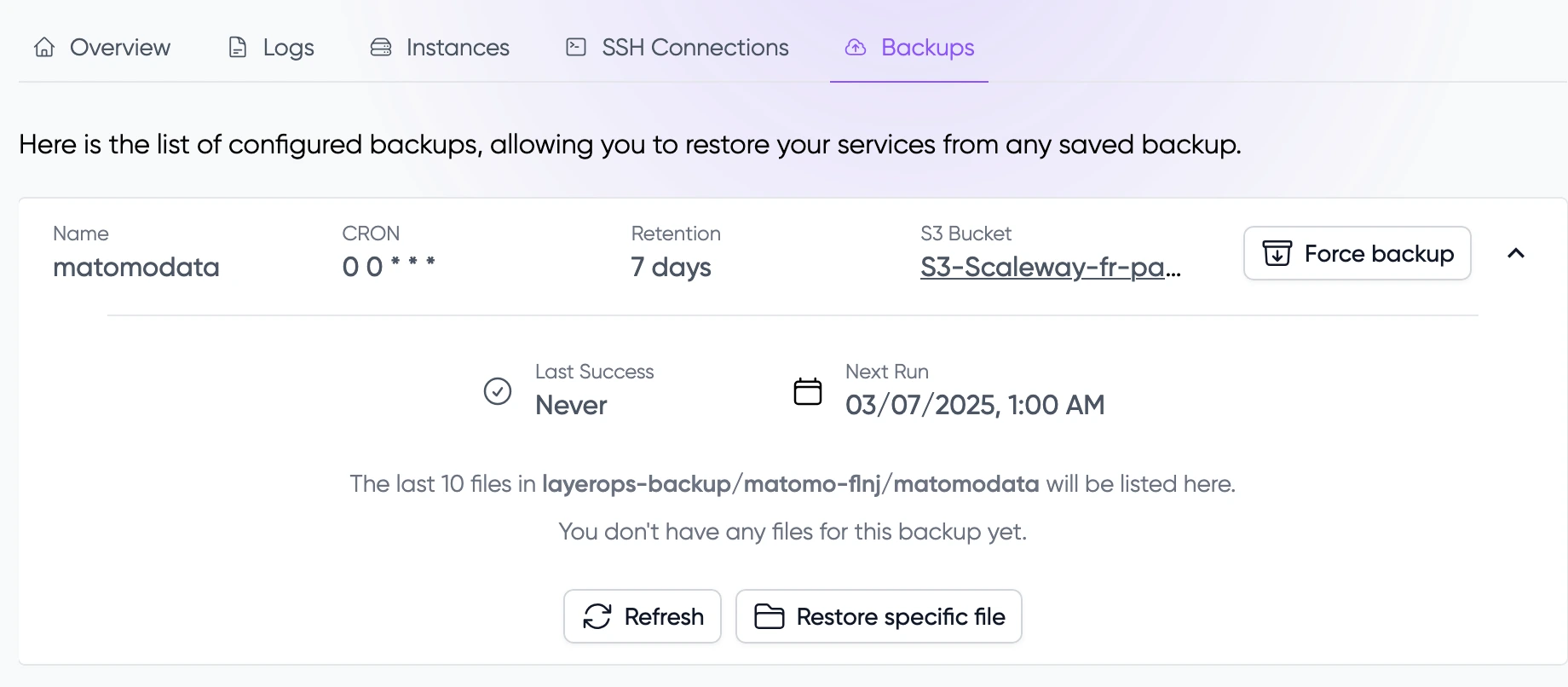
Backups
The "Backups" tab allows you to manage backup configurations for your service volumes or databases. From this interface, you can:
- Monitor all backup configurations
- View backup schedules (configured with CRON expressions)
- Check retention periods and destination S3 buckets
- Track the status of recent backups
- Trigger immediate backups
- Restore from previous backup versions
- Refresh the list of available backups from your S3 storage